AISD SFA & THS Campus Network
Faculty Reference Manual
(c)1999 Vernon Graner CNE
Created October 2nd, 1997
Last Upate Sept 29th 1999
!DRAFT VERSION!
Table of contents
Network System Overview
SFA Campus Description
The SFA Campus Computer Network consists of multiple DOS/Windows and Macintosh based computers connected via Ethernet to a central file server running Novell Netware (complete system specs included in the appendix) Most of these computers are multimedia ready Pentium systems with color monitors and shared printing. The machines are setup as follows:
- Room 125: 30 AGAMA W95 Pentium 133 workstations w/sound & CDROM. (w/attrition ~25)
- Room 309: 31 Dell Optiplex Pentium 166 W95 workstations w/sound & CDROM.
- Room 310: 31 Dell Optiplex Pentium 166 W95 workstations w/sound & CDROM.
- Room LIB: 43 Dell Optiplex Pentium 166 W95 workstations w/sound & CDROM.
- Room CCC: 6 ~Pentium 66 donated workstations.
- Room 152: 5 Dell Optiplex workstations w/sound & CDROM.
- Room ???: Macs (help on this section from Johnathon?)
THS Campus Description
The THS Campus Computer Network consists of multiple DOS/Windows and Macintosh based computers connected via Ethernet to a central file server running Novell Netware (complete system specs included in the appendix) With the exception of room 407, Most of these computers are multimedia ready Pentium systems with color monitors and shared printing. The machines are setup as follows:
- Room 401: 34 Dell Optiplex Pentium 166 W95 workstations w/sound & CDROM.
- Room 405: 31 STS W95 AMDK6 300 workstations w/sound & CDROM.
- Room 407: 32 Compaq 486-66 W95 workstations.
- Room 406: 30 Mixed Dell Optiplex, IBM & Gateway Pentium workstations (some w/sound & CDROM.)
- Room 300: 8 Macintosh G3 computers (?)
- Room LIB: 31 STS W95 AMDK6 300 workstations w/sound & CDROM. (no speakers)
- Room ???: Macs (help on this section?)
In addition to the programs provided with Windows 95, each machine has the Microsoft Office Professional suite of programs consisting of Microsoft Word, Microsoft PowerPoint, Microsoft Excel and Microsoft Access. All programs are dellivered through the Novell ZEN application launcher. User files are kept on the file server and applications are kept on the local hard drives. Most rooms have shared printing some have color printers others have laser. Complete detailed descriptions are available in the appendix.
The network uses a combination of products to provide an unusually high level of availability to the campus. It should be noted that the process used makes the local hard drive (c:) expendable. All the contents of the local hard drive (c:) is forfeit when regular maintenaince is performed on the machine.
NOTE: The Macintosh computers connection to the network is only to provide them with Internet access. No system management settings or user files are kept on the Novell servers at this time.
Student Lab policies
The computer lab policies to be presented to the students are reproduced here for your reference. A single page printable/postable version is available in the appendix.
- No food or drink may be present at any workstation.
- Program may be run without the authorization of the instructor.
- No floppy disks are to be used without the permission of the instructor.
- No materials are allowed at the workstation other than those required for the course (Backpacks, book bags etc. should be left in the designated area by the door)
- No one may adjust any of the controls associated with their workstation including but not limited to:
- Windows 95 settings
- screen blanker settings
- Video Monitor controls
- Speaker Volume
- No student may attempt to fix or repair any operational problems with a workstation. Any problem should be reported immediately to the instructor.
- Each student must log out of their workstation before leaving.
- Each student must replace the keyboard, mouse, mouse pad and chair to their original positions before leaving their workstations.
Violation of any of these policies may result in the student being expelled from class and their receiving a failing grade (zero) for the course.
Faculty Lab policies
(Adapted from the Business Department Policy drafted by Guy Davis)
Policy on the Teacher's Computer
- Students are not allowed to operate a computer that is logged in with a faculty account unless the faculty member is directly supevising them.
- The teacher should not allow access of their account to any student.
Policy for changing the configuration of each computer.
- The system administrator must make any changes to the configuration of each computer.
- The system administrator will be the only person to add programs to the network.
- Students are not allowed to reconfigure, add or change any software to any computers on the network or in the classroom.
- All software installation requests to the system administrator will be accompanied by proof of adequate licensing.
- Any software that is judged by the system administrator to compromise security on either the computer or the network will not be installed.
- Shared use labs (computer labs used by more than one instructor) must be left in as close to the exact hardware/software configuration as they were found.
Policy on using the requirements for each course.
- Only the TEKSs should be taught in each class.
- Other information that does not have a direct bearing on the TEKs should not be covered in that class.
Policy on student files
- Student files should be monitored for appropriateness and conformity with the AISD AUP.
- Any inappropriate files will result in:
- Immediate suspension of their account.
- Removal from class.
- Incident reported to campus technology coordinator
- Student files should be deleted after the relevant assignment is graded.
Policy on Lab Maintenance
- Any system failures that cannot be solved with either an application "verify" or a LAZARUS operation should be noted in a "Trouble Ticket" and delivered to the Camps Technology Coordinator.
- The system administrator will collect "Trouble Tickets" from the Campus Technology Coordinator and repair systems in "triage" order.
- Any teacher may make minor computer repairs (i.e. replace a mouse).
Drive Letters
Once you have logged into the file server as a Faculty member, you will have access to the file server resources such as shared printing and new drive letters. The following table shows each drive letter available to a properly logged in faculty member along with its intended use.
|
A:
|
Local 3.5" Floppy: Floppy drives can be used to transport data between lab and home computers. To synchronize files use the Briefcase icon on the desktop. (For more information of the briefcase, open the briefcase icon and choose the HELP menu. From there, choose the INDEX tab and type BRIEFCASE in the first blank.)
|
|
C:
|
Local hard drive Do not use this drive! Do not store any data on the local C drive. The contents of this drive are completely erased in some maintenance functions! Do not use this drive. Save important data in your home directory (H:) only!
|
|
D:
|
Local CDROM Used to run programs from CDROM. May be used to play standard music CD's as well.
|
|
F:
|
Network Login: Do not use this drive! The network reserves this drive for DOS based logins. You should not use this drive unless instructed to do so by the Network Administrator.
|
|
G:
|
Students Shared All students can see and read from this drive but cannot write to it. This drive is a good place for instructors to place instructional or example files for distribution to all students.
|
|
H:
|
User Home: Each logged in user can read, write, create, edit and modify any files placed in their home directory. Only the user or the System Administrator can see the contents of this drive.
|
|
I:
|
STUDENT VIEW: Each student's home directory is visible here as the period number followed by the seat number (IE: period 1 computer 12 would be directory 112)
|
|
J:
|
Network Applications: Any applications that are stored on the network and designated for shared use are available here (IE: Turbo Pascal)
|
|
L:
|
Faculty Shared: All users logged in as Instructors or System Administrators can read, write, create, edit and modify any files placed here. This drive is a good place for instructors to place material they want to share with other instructors. Only users logged in as Instructors or System Administrators can see the contents of this drive.
|
|
Z:
|
Network Public Do not use this drive! Network Oriented commands are kept here. You should not use this drive unless instructed to do so by the Network Administrator.
|
Network Access
Logging In
To login to the AHS computer network, follow these steps:
- If the computer is not powered on, power it on and wait for a requester box labeled WARNING.
- Click OK on the WARNING requester box. (You will be prompted for a name and password.)
- When the Novell Client login box (shown below) appears, Enter your login name in the USERNAME box.
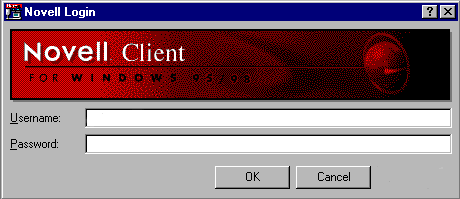
Note: Your login name is derived by your first initial followed by up to 7 letters of your last name, followed by .fac.campus.aisd. IE: Vernon Graner is vgraner.faculty.sfa.aisd on the Austin High campus or vgraner.faculty.ths.aisd on the Travis campus
- Press the TAB key to move to the PASSWORD box.
- Type your password.
- Press return or click OK.
You should now be successfully logged in.
Logging Out
It is very important to network security that an instructor log out of the network every time they leave their workstation! The privileges given to faculty accounts would allow any student to easily damage or destroy important data on the network or to subtly alter files in the name of the instructor. Such damage is virtually untraceable. To log out of the network follow these steps:
- Save any work files you may have opened
- Close all open applications
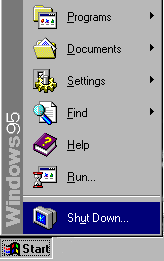
- Click the START button in the lower left corner
- Select SHUTDOWN from the menu (Shown Below) that appears
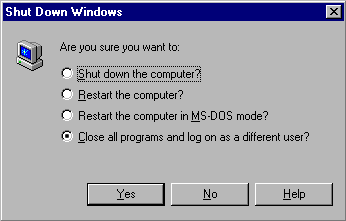
- When the Shut Down Windows requester (Shown Below) appears, choose Close all programs and log in as a different user
- Choose YES
You should now be successfully logged out.
Guest User Access
(Note: For advanced users!)
In the event a user needs immediate temporary access to a computer during a class period, they may log in as ASTUDENT with a password assigned by the instructor. This account may also be used in the event of a student forgetting a password. It should be noted that a student's home directory files will not be visible if they are logged in as a guest user unless the instructor copies the student's files to the guest account. To copy student files to the guest account, follow these steps:
- Login as a faculty member on any computer (preferably the designated teacher workstation at the front of the class)
- Use Windows Explorer to navigate to the I: drive
- Access the student home directory
- Copy the needed files to the clipboard
- navigate to the astudent directory
- paste the files into the guest account
Passwords
Expired Passwords
To insure network security, the server is set to automatically expire your password every six weeks. You may not use the same password more than once. You have 9 'grace' logins that allow you to login with an expired password without changing it. Once you have used all 9 grace logins, your password will not allow you access to the network. If you receive a message stating your password has expired, follow the steps here to change it:
- Click YES on the "change password now? " requester.
- Click into the box labeled NEW PASSWORD
- Type a new password
- Press TAB to move to the verification box
- Type your new password in the verification box
- Press return or click OK
You should get a confirmation requester that indicates your password was successfully changed. If you do NOT get this requester, repeat steps 2 through 6 above.
Student Passwords
When a student logs in for the first time, they will be informed that their password has expired and they will be prompted to enter a new password (for information on how this is done refer to the section entitle
Password). In order to insure that the student does not forget their password, the students should be supplied with a password slip (example is attached as). After the student has entered their password, they should write it on this password slip, fold it in half and then give it to the instructor. This will allow the instructor to look up the students' password in the event of loss.
The instructor should stress the concept of password security by encouraging the student to remember the password and not to share it with other students. Sharing passwords is a violation of the student lab manual and is grounds for expulsion from class with a failing grade!
If a student is unable to login to their account for some reason, and the system administrator is not onsite, the instructor may fill out a trouble ticket to request the account be reset.
Creating Student Accounts
Each student must have a student account created before they may use the network. The examples show in the illustrations below use the Travis High School campus room numbers and periods. If you are creating accounts at the Austin campus, substitue the appropriate room number and classroom. To create a student account follow the steps as outlined here:
|
Log in with your faculty account then launch NWAdmin by clicking the icon in the system tray as shown here.
|
|
You must navigate to the location of the classroom you will be creating accounts for. Click as shown to begin.
|
|
Choose the BROWSE button as shown here:
|
|
|
|
Choose the Room where you want to create a student account. (Note: You may only create student accounts in rooms where you are the RoomAdmin!)
|
|
|
|
|
|
|
|
|
|
|
|
|
Troubleshooting
System Lockups
The network workstations use a combination of Windows 95 and Novell Netware for all operations. Windows 95 may open many files on the local hard drive and on the file server in the course of carrying out your commands. If these files are not closed in an orderly manner, they can be lost or damaged. It is therefore important that every effort be made to allow Windows 95 to close all files it may have opened before power is shut off.
If you have a machine that appears to have "locked up" (no programs appear to be responding or processing), follow these steps before resorting to a power cycle*.
- Test for responsiveness by pressing the CAPSLOCK key a few time to see if the CAPSLOCK LED turns on and off. If the LED does not respond the system is either VERY busy or could be locked up.
- Press CTRL-ALT-DELETE and see if a requester with all running program shows on the screen. If it does you may end the program that appears to have locked up or you can choose SHUTDOWN from the requester to try and close Windows properly.
If none of these suggestions work a power cycle* may be required.
Problem Solution Table
|
Problem
|
Explanation/Possible Cause
|
Solution
|
|
Computer monitor's Screen is black and its power light is yellow.
|
The computers in the lab use GREEN-PC power saving functions. After 60 minutes of idle time (measured from the last time a keyboard or mouse event was received) the computer will enter 'sleep' mode and the monitor will power off. The screen will turn black and the power light on the front of the monitor will be yellow.
|
To 'wake up' the computer from its 'sleep' mode, move the mouse or press the spacebar. You will hear a soft 'crackle' sound as the monitor powers up and the picture should fade in. If the monitor does not come on, check to see if the computer has been powered off. (The number on the video monitor corresponds to the number on the computer). Check to see if the topmost green LED is lit. If not, check to see if the power switch has been turned off or the power cord has come unplugged.
|
|
The mouse pointer is frozen in place on the computer monitor.
|
Sometimes the computer system can become "locked up" due to static electricity, program failure or any number of other Windows-related problems. Though not usually an everyday occurrence, this symptom is usually easily cured.
|
Check to see if the mouse ball is present! Check to see if the mouse cord is connected to the computer. Try all the steps in the System Lockups section detailed above before resorting to a power cycle*. If the computer still exhibits the symptom, fill out a trouble ticket for the System Administrator
|
|
The computer shows GENERAL PROTECTION FAULT or ILLEGAL OPERATION message in white letters on a blue screen or in a requester box.
|
The program you were using has reached an unstable state. (AKA Crashed) This can be caused by an error on the part of the programmers who made the program or operating system to something as innocuous as static electricity or a small power surge.
|
Close the requester and then click START / SHUTDOWN / RESTART computer. If after restart the computer still exhibits the symptom, try a power cycle*. If the problem persists, fill out a trouble ticket for the System Administrator
|
*To Power Cycle a computer: Wait a few minutes for the computer activity to cease. If possible shut down Windows either through a START/SHUTDOWN COMPUTER or through a CTRL-ALT-DELETE/ SHUTDOWN COMPUTER. When the computer shows a "IT IS NOW SAFE TO TURN OFF YOUR COMPUTER" message on the screen, turn off the power by pressing the POWER button on the front of the computer. Wait about a minute and then turn the power back on.
Appendix
A. Network System Technical Specification
B: Student Password Slip
C. Contact List
D. New Program Request
E. Trouble Tickets
Stephen F. Austin
Network System Technical Specification
AGAMA Workstations (Square bottom towers) Rm 125:
- Pentium 133Mhz processor
- 256k Pipeline Burst Cache, 3 PCI/ 4 ISA Motherboard w/ Award PNP BIOS & Embedded IO
- 16 Megs EDO memory (2x8m 72p SIMM 2 sockets open)
- 1.44 Floppy Drive
- Two 16550 UART High Speed Serial ports (one used for serial mouse)
- One EPP Parallel Port
- Dual PCI/EIDE drive ports
- 1.6GB EIDE PIO Mode 4 Hard Drive
- 8X ATAPI IDE CDROM Drive
- Diamond Stealth PCI 2Meg SVGA card set @ 800x600x16.8m colors
- 16 Bit Realtek PNP NE2000 Compatible ISA Ethernet Combo TP&BNC Card (TP used)
- 16 Bit PNP OPTI Soundblaster Pro Compatible ISA Sound Card W/MPU 401 MIDI emulation
- GVC 15" Non interlaced GREEN PC VESA compliant Video Monitors
- Adjustable volume stereo speakers (attached to monitors)
- 101 Key Keytronic Keyboard
- Mitsumi 2 button Microsoft compatible serial mouse
C1 Workstations (Round bottom towers) Rm 125 & Library:
- Pentium 133Mhz processor
- 256k Pipeline Burst Cache, 3 PCI/ 4 ISA Motherboard w/ Award PNP BIOS & Embedded IO
- 16 Megs EDO memory (2x8m 72pin SIMM 2 sockets open)
- 1.44 Floppy Drive
- Two 16550 UART High Speed Serial ports (one used for serial mouse)
- One EPP Parallel Port
- Dual PCI/EIDE drive ports
- 1.6GB EIDE PIO Mode 4 Hard Drive
- 8X ATAPI IDE CDROM Drive
- Diamond Stealth PCI 2Meg SVGA card set @ 800x600x16.8m colors
- 16 Bit Realtek PNP NE2000 Compatible ISA Ethernet Combo TP&BNC Card (TP used)
- 16 Bit PNP OPTI Soundblaster Pro Compatible ISA Sound Card W/MPU 401 MIDI emulation
- GVC 15" Non interlaced GREEN PC VESA compliant Video Monitors
- Adjustable volume stereo speakers (attached to monitors)
- 101 Key Keytronic Keyboard
- Mitsumi 2 button Microsoft compatible serial mouse
Dell Workstations (Desktop Gs+ units) Rm 309, 310 & Library:
- Pentium 166Mhz processor
- 512k Pipeline Burst Cache, 3 PCI/ 4 ISA Riser-Motherboard w/ DELL PNP BIOS & Embedded IO
- 32 Megs EDO memory (2x16m 72p SIMM 2 sockets open)
- 1.44 Floppy Drive
- Two 16550 UART High Speed Serial ports
- One EPP Parallel Port
- PS2 Mouse port (used for DELL/Logitec mouse)
- Dual PCI/EIDE drive ports
- 1.6GB EIDE PIO Mode 4 Hard Drive
- 24x ATAPI IDE CDROM Drive
- Embedded PCI video 2Meg SVGA card set @ 800x600x16.8m colors
- 16 Bit 3Com PNP 3c509 Compatible ISA RJ-45 Ethernet embedded on Motherboard
- 16 Bit PNP Soundblaster VIBRA ISA Sound Card W/MPU 401 MIDI emulation (in ISA slot)
- DELL 15" Non interlaced GREEN PC VESA compliant digital-control Video Monitors
- Adjustable volume stereo speakers (available from room admin)
- 101 Key DELL PS2 Keyboard
- Logitec 2 button Microsoft compatible PS2 mouse
File Server:
- AMD K6 200mhz processor
- 256k Pipeline Burst Cache, 3 PCI/ 4 ISA Motherboard w/ Award PNP BIOS
- 96 Megs EDO memory
- 1.44 Floppy Drive
- 2 16550 UART High Speed Serial ports
- 1 EPP Parallel Port
- Adaptec 2940W PCI SCSI Adaptec
- 2GB SCSI II & 3GB SCSI II Hard Drives
- Colorado 4gb TR4 tape backup unit
- Four 8X ATAPI IDE CDROM Drives
- Trident ISA VGA
- 3COM 3c900 PCI 10mb Multimode Ethernet Card (TP&BNC W/BNC used to connect to hubs)
- GVC 15" Non interlaced GREEN PC VESA compliant Video Monitors
- 101 Key Keytronic Keyboard
Network System:
- Twisted pair category 5 plenum certified Ethernet cabling
- 16port Ethernet Switch connecting all segments.
- Hewlett Packard JetDirect EX Print Servers
- HP Laser Printers
- HP Color Inkjet Printers
Contact List
If you need assistance with a computer issue, these are the contacts.
|
Function
|
Name
|
Phone
|
Email
|
|
Network Engineer Novell/Wintel support
|
Vernon Graner CNE
|
624-6062 Pager 328-8947 Office
|
vern@txis.com
|
|
Network Administrator Macintosh Support
|
Johnathon Arehart
|
|
arehartj@io.com
|
|
Campus Technology Coordinator
|
Bill Glover
|
414-7206 Office
|
bglover@tenet.edu
|
|
Business Dept Chair
|
Guy Davis
|
414-7380 Office
|
gkdavis@swbell.net
|
|
Faculty Account Administrator
|
Angie Reeves
|
414-xxxx Office
|
|
 D. New Program Request
D. New Program Request
Network System
COMPUTER LAB NEW PROGRAM REQUEST
E. Trouble Tickets
STEPHEN F. AUSTIN HIGH SCHOOL
COMPUTER LAB TROUBLE TICKET
Instructions: Fill in all fields as completely and legibly as possible. When completed, deliver the form to the System Administrator, either in person or by sliding the form under the System Administrator's office door.
Today's Date: Period:
Computer # or Location:
Date problem first detected:
Instructor:
Is the machine disabled due to this problem?
o Yes o No
Is the problem reproducible?
o Yes o No
Steps to reproduce problem:
EXACT WORDING of error message, if any:
Other comments:


 D. New Program Request
D. New Program Request